
Password manager Passwordstate hacked to deploy malware on customer systems
A mysterious threat actor has compromised the update mechanism of enterprise password manager application Passwordstate and deployed malware on its users’ devices, most of which are enterprise customers.
Click Studios, the Australian software firm behind Passwordstate, has notified its 29,000 customers earlier today via email.
According to a copy of the company’s communications, obtained by Polish tech news site Niebezpiecznik, the malware-laced update was live for 28 hours between April 20, 20:33 UTC and April 22, 00:30 UTC.
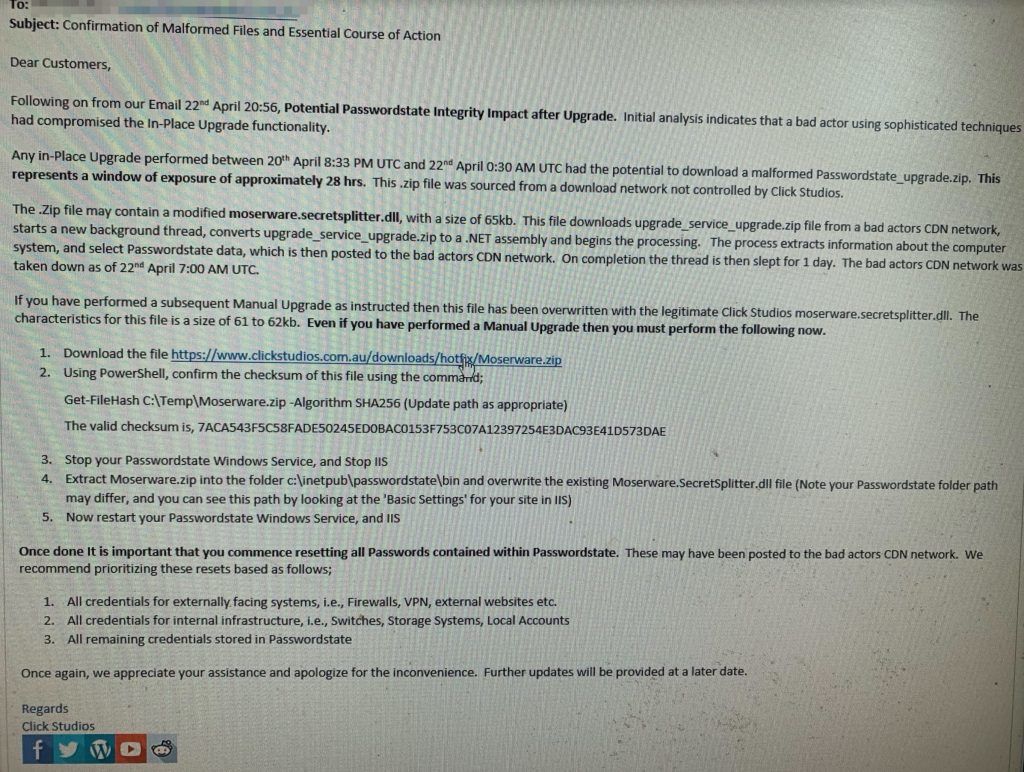
Danish security firm CSIS, which dealt with the aftermath of this supply chain attack, published today an analysis of the attacker’s malware. The security firm said the threat actor forced the Passwordstate apps to download an additional ZIP file named “Passwordstate_upgrade.zip” that contained a DLL file named “moserware.secretsplitter.dll.” After installation, this DLL file would ping a remote command and control server, from where it would request new commands and retrieve additional payloads.
While initially it was unknown what attackers collected from infected systems, in two updates [PDF, PDF] published after this article went live, Click Studios said the malware collected the following information and sent it back to its command and control server:
Computer Name, User Name, Domain Name, Current Process Name, Current Process Id, All running Processes name and ID, All running services name, Display name and status, Passwordstate instance’s Proxy Server Address, Username and Password
In other words, the password store was taken. According to the Australian company, the following information is typically included in the password table:
Title, UserName, Description, GenericField1, GenericField2, GenericField3, Notes, URL, Password
Although the company said “there is no evidence of encryption keys or database connection strings” were taken, Juan Andres Guerrero-Saade, Principal Threat Researcher at SentinelOne, pointed out on Twitter, that there are tools currently available that can decrypt the Passwordstate vaults and recover cleartext passwords.
Click Studios released a hotfix package [ZIP] that would help customers remove the attacker’s malware, which the company named Moserware. [instructions are in the image above]
Click Studios said the hack took place after a threat actor compromised the “In-Place Upgrade functionality” of a CDN network not controlled by Click Studios. Only the company’s Windows client appears to have been modified to add malware in the attack.
29,000 companies now have to rotate passwords
In the aftermath of this security breach, the Australian firm has told customers to change all the passwords they stored inside compromised Passwordstate password managers as soon as possible.
Since this is a password manager is sold primarily in bulk to enterprises, to whom it is advertised as an on-premises system, changing passwords won’t involve just email and website accounts, but also passwords for internal gear such as firewalls, VPNs, switches, routers, network gateways, and others, which many employees would most likely have saved inside the app thinking it was a secure local storage system.
“This is a real annoying breach,” William Thomas, a malware analyst at UK security firm Cyjax, told The Record. “Imagine having to change all your passwords for each device on the network, on a Friday.”
Several network administrators have told The Record on Friday that they had to work over the weekend to change the passwords of all their IT inventory as a result of the breach. Many companies also intend to activate incident response plans to check logs for unauthorized access as a result of this incident as well, resulting in many overtime hours for their already swamped security personnel.
Comments












